Offensive Security Foundations for Financial Industry Professionals
Security Standards (PCI DSS) are vital in establishing baseline security measures for financial...
Control Gap is expanding our Offensive Security team and looking for talented individuals. To ensure that we have the right team, we needed a better way to evaluate potential candidates. Interviews are only one lens to get to know a person. However, we felt we needed to elevate our selection process ensure that our candidates felt they were truly the right fit for Control Gap.
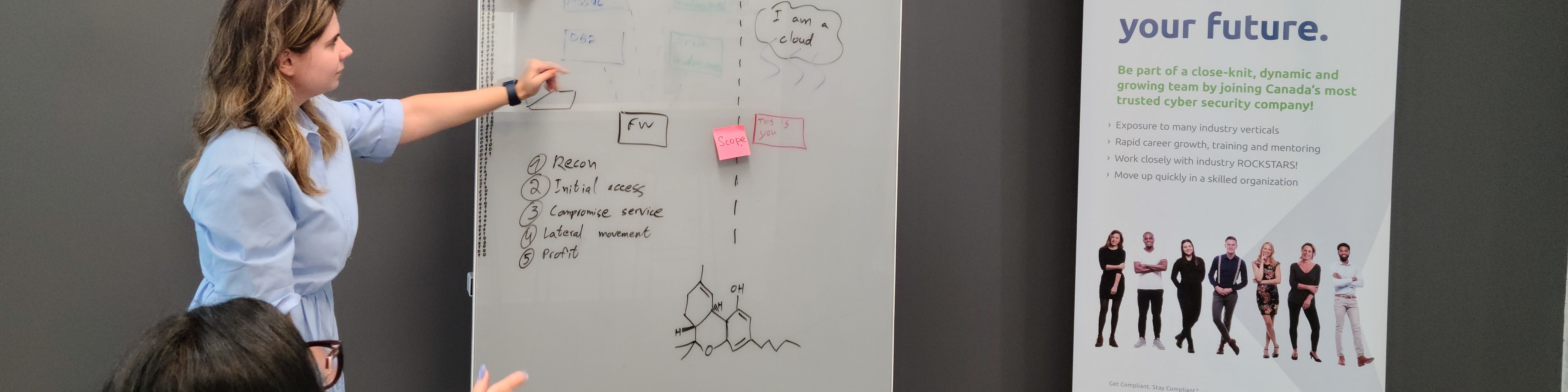
The old way of evaluating Offensive Security candidates’ capabilities needed improvement. Whiteboard challenges don’t show an individual’s true potential. Something more was needed. Something to better measure performance and capability in realistic scenarios. Something to separate skills and capabilities from the pressures of interviews.
We could ask for sample reports, but what if the candidate is not allowed to share proprietary and obviously sensitive documents? Redacted penetration test reports could be useful but there’s a risk of missing sensitive 3rd party information.
Many organizations use “Hack-the-Box” to qualify candidates. Some of these machines are difficult and similar to what you would expect to find in an actual penetration test, but we have no control over them, and most solutions have been published.
The bottom line is that no matter what and how many technical questions we might ask in an interview, there will always be the sense of pressure.
“Control Gap’s robust hiring process was further validation that this was the right organization for me.” -Connor McMillan, Lead Offensive Security Consultant
We wanted a hiring approach that grew progressively to cover the breadth of technical skills.
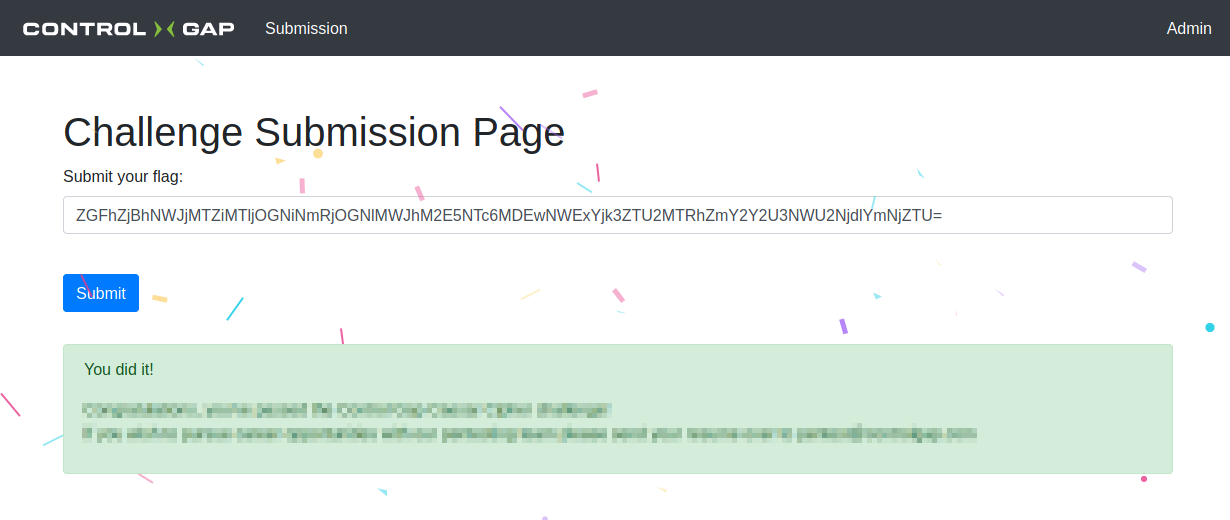
We use our simple web challenge as an initial indicator of the candidate’s approach and capabilities. Nothing is restricted and there is no allotted timeframe. It is always on, and anyone can open the URL to try their luck. Go Ahead, give it a try: https://ctf.controlgap.io
You completed the first challenge! Great job. Now let’s talk about it: What was your process? Would you have done anything differently? Did you enjoy it?
Now this is where it gets a little bit tricky. Our custom-built vulnerable machine offers candidates the opportunity to explore and demonstrate their hacking skills in an environment that more closely resembles what they’ll encounter in the day-to-day activities of an offensive security consultant.
![]()
Our vulnerable machine was specifically built in a way to have multiple vulnerabilities throughout the environment and to allow for various exploits, to see how far the candidate can get.
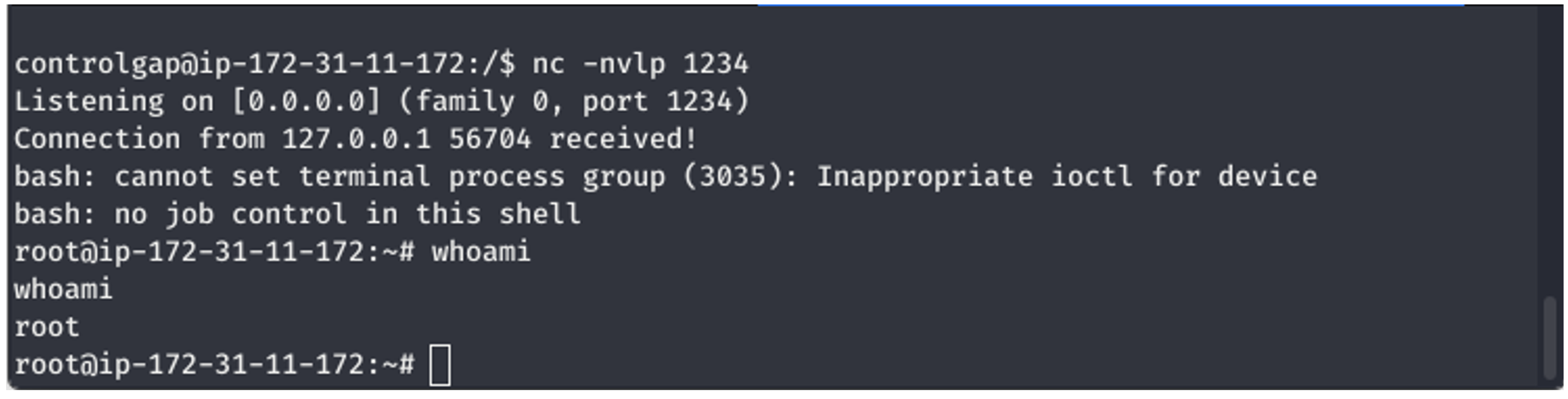
The time is limited, and access is provided independently to each candidate. They will be required to manage their time accordingly, mind the rabbit holes, and communicate in the event of any potential issues.
“Ample time to run through the playground and flex your skills, nothing too CTFy, reasonably representative of the real world. Often companies just lazily resort to a random hack-the-box and then watch you do it, which is the worst.” -Konrad Haase, Lead Offensive Security Consultant
The candidate will be required to submit a final report, which will include all the findings and associated recommendations, as they would in an actual engagement. Eventually, the delivered report will be evaluated on all its aspects. This gives us the opportunity to have better insight to the process, capabilities, and perseverance of each person.
Taking a completely different approach to validating a potential candidate gives our team the ability to focus their energy on identifying the right balance of skillsets, experience, and customer service. Our candidates are not pressured into memorizing answers to technical questions, but rather spread their wings and show us the amazing talents they have.
Through this process we can select the best talent to ensure that our customers feel we’ve done the right job and our team can positively affect change that will have significant downstream impacts to make a safer cybersecurity world.
For more information about current opportunties and how to join our team please see https://controlgap.com/careers
For more about us please see https://controlgap.com/about-us/
.png)
 CG Blogger :
Oct 16, 2024 12:00:00 AM
CG Blogger :
Oct 16, 2024 12:00:00 AM
Security Standards (PCI DSS) are vital in establishing baseline security measures for financial...

 Ben Rediboim :
Dec 9, 2020 10:07:00 PM
Ben Rediboim :
Dec 9, 2020 10:07:00 PM
Attention Windows sysadmins: search for "LLMNR" and once you've finished panicking, then get that...

For organizations running on-premise Microsoft Exchange servers, we want to make you aware of...