PCI DSS v3.2.1 - What You Need to Know to Stay PCI Compliant
To accept credit cards in Canada, businesses need to be PCI compliant. Becoming PCI compliant can be difficult in the first place and keeping up...
7 min read
 David Gamey
:
Jan 28, 2019 10:07:00 PM
David Gamey
:
Jan 28, 2019 10:07:00 PM

Big changes are coming to payment security in 2019. PCI is launching a grand experiment in payment security - Software PIN on COTS (SPoC) - a subset of "PIN-on-glass". SPoC is intended to make payments using devices like phones and tablets both easy and secure. The approach is both interesting and a departure from previous payment security standards. SPoC has generated a lot market interest but will face challenges with complexity and potentially with acceptance. This article looks at what SPoC is, its new security model, and some of the challenges. We also present a timeline on the standard including known mandates.
The PCI Council which oversees 10 different standards and a dozen programs is in the process of updating and rolling out standards that will have a big impact on payment security. In addition to SPoC, 2019 will see a new software security standard & framework to replace PA-DSS, improvements to the 3DS standard to benefit card-not-present & mobile payments, a new Qualified PIN Assessor (QPA) program, and a Contact-less payments on COTS standard.
Simply put, PIN-on-Glass is a general payments use case where a customer PIN is entered on the merchant's touch screen. This includes both certified payment terminals and also non-certified solutions. Software PIN on COTS (Commercial-Off-The-Shelf) is a use case where the customer PIN is entered into a commercial device like a phone, or tablet while the card is processed via small secure device.
There are two main concerns that arise from the new form factor and the new architecture these are:
From a security perspective, PTS approved touch screen payment terminals already exist and are there are no additional security complications. Securing a PIN entered into any general purpose computing device is challenging to say the least. At this time, there are exactly zero certified SPoC solutions! There are however, many uncertified solutions - many of which are insecure.
From an accessibility perspective, with any PIN on Glass or SPoC solution merchants need to do their due diligence as they may find themselves on the wrong end of a legal action if they cannot accommodate customers with disabilities.
We will discuss all of these later in the article.
SPoC is, at least in part, a response to initiatives by companies like Square. The existing PCI software standard, PA-DSS, simply didn't and couldn't support this use case. In fact, payment applications for COTS devices are specifically not permitted under PA-DSS. The only approved mobile security model for PCI prior to SPoC was to use a mobile POS with a P2PE approved terminal solution rendering the COTS mPOS out of scope.
SPoC is a radical departure and required completely rethinking the approach to software security. The basic idea behind SPoC is to reduce risk by splitting up sensitive data, actively monitor the operation of the solution, and react in real-time. By supporting EMV, SPoC also rejects the use of static authentication data (i.e. magnetic stripe). The approach buys security at the cost of additional monitoring and attestation complexity.
SPoC solutions consist of several parts:
An approved SPoC Solution
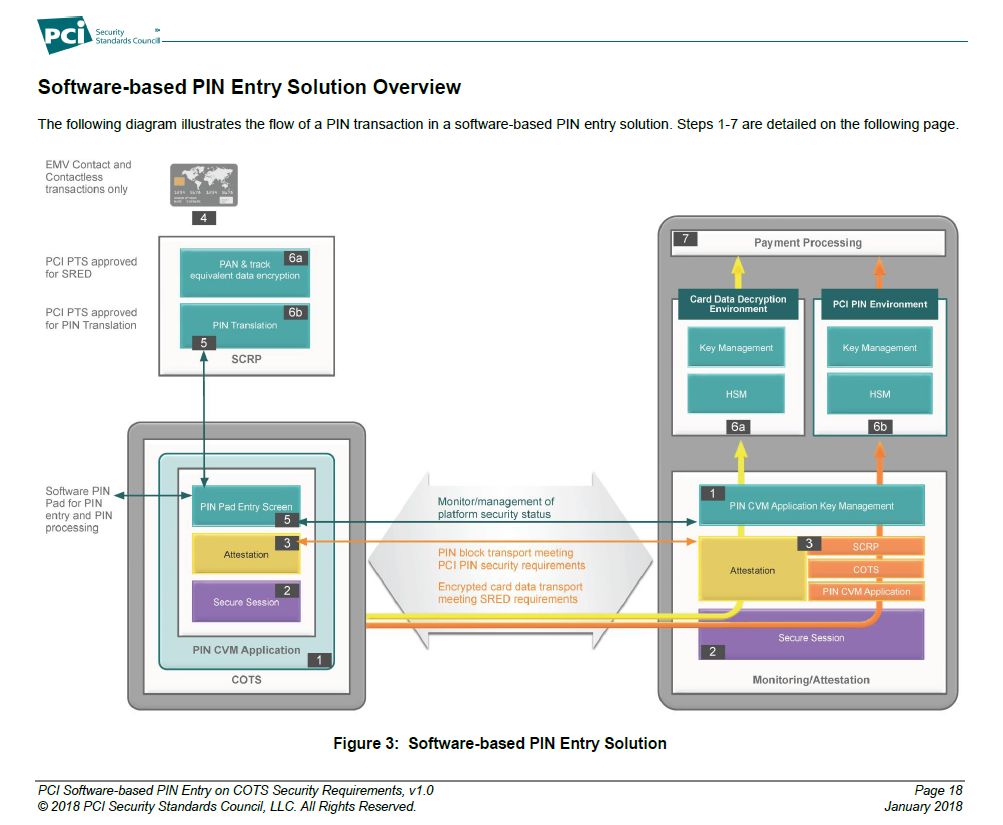
The SCRP connects to the COTS device and provides:
The PIN CVM application running inside the COTS device provides:
The back-end provides:
SPoC is a buying tool for merchants and consumers. In addition to using approved PTS SCRP devices, solution providers will need to validate the PIM CVM and backend software with an approved SPoC lab. The solution provider's back-end environment will also be validated against the enhanced PCI DSS requirements known as DESV.
The following diagram from the PCI Council illustrates the architecture:
Many jurisdictions, including the US, Canada, and the EU, have laws aimed at providing accessibility for disabled individuals. The scope and breadth of these laws varies. While a merchant using SPoC "line-busters" backed up by traditional PIN pads should have no problems, a merchant offering payment only via SPoC could be at risk under many of these laws as there have been a number of lawsuits filed in the US over the use of touch screens and apps.
Learn more:
Regardless of demand, a percentage of the population may simply refuse to trust these solutions. This is particularly true in places that have had active "Protect your PIN" awareness programs.
Buy-in from other payment networks could be an important factor. Just because the major card brands are on-board doesn't mean that other payment networks will be.
The Canadian market is a good example of where PINs are more strongly associated with the major banks, trust companies, credit unions, and Interac, the national ATM and debit network, which took an early lead in promoting EMV and contactless payments than brands like Visa and MasterCard. The Canadian experience with PIN based magnetic stripe credit card payments has been almost non-existent. Canadians are very comfortable with using PINs for payment which may help adoption. However, the success of SPoC in Canada will be heavily influenced by whether or not Interac buys into SPoC and how protective Canadian consumers feel about their PINs.
It is also unclear if recent trends in data breaches will dim enthusiasm for this type of solution.
SPoC is designed with defense in depth in mind.
One of the more radical parts of SPoC is the PIN CVM monitoring. The ability and effectiveness of active tamper detection mechanisms designed to ensure that phones and tablets will not be run jail-broken or with debuggers remains an open question.
In order for a criminal to get both your card data and PIN, they would need to compromise or replace both the SCRP device and the PIN CVM application. The use of fake or non-compliant card readers and PIN CVM applications presents the largest risk to consumers using SPoC.
A number of existing non-certified COTS card readers are known to be insecure. Recent tests of Bluetooth enabled payment devices used by Square, PayPal, Zettle, and SumUp finds lots of vulnerabilities https://www.forbes.com/sites/thomasbrewster/2018/08/09/these-bluetooth-hacks-can-steal-your-credit-card-pin/
By limiting SPoC to EMV only and eliminating the use of static authentication data (i.e. magnetic stripe) the risk should be reduced.
Consumers will be hard pressed to identify a legitimate SPoC device. The exclusion of magnetic stripe readers (MSR) provides a a teachable point as the presence of an MSR should raise a huge red-flag that the device is not certified. However, a proposal under consideration to allow pin-less MSR on SPoC may jeopardize this important clue.
The PCI Council does not set compliance deadlines as these are left to the individual card brands. For instance, there are no requirements within PCI DSS to use certified SPoC solutions. However, without them the heavy burden of compliance proof will fall to the merchant.
Visa has announced a mandate to sunset all non-approved SPoC solutions:
PCI Software-based PIN Entry on COTS Device Standard and Program Published REGIONS: US, AP, Canada, CEMEA, LAC, Europe 26 JUL 2018
The Payment Card Industry Security Standards Council (PCI SSC) has published a standard for protecting PIN-based transactions on commercial off-the-shelf (COTS) devices. Merchants accepting PIN-based transactions via COTS devices must use or transition to a PCI-validated software-based PIN entry on COTS solution by 31 July 2019.
Source: https://usa.visa.com/support/merchant/library/visa-merchant-business-news-digest.html
Realistically, implementing new payment systems at acquirers and merchants can take months. With no available certified solutions and only seven months to the sunset date, the deadline seems unrealistic.
In the original release of the standard, MSRs were completely excluded. Last week the PCI Council announced that it is considering some form of transitional support for non-PIN magnetic stripe transactions. A 90-day feedback cycle will begin on this shortly.
For more information see the announcements for SPoC and Contactless in 2019 https://blog.pcisecuritystandards.org/pci-spoc-and-contactless-standards-what-to-expect-in-2019/
Innovation and security frequently seem at odds. Tension between the promise of bright shiny new tools, and the rigor needed to ensure they're secure seems constant. Easier, faster, and more powerful things can be exploited by those with both good intentions and bad. Over the last decade payment software has been changing far more rapidly than the approved security framework increasing the tension. PCI SPoC is a radical departure from PA-DSS. SPoC represents a new approach and an attempt to strike a new balance between payment innovation and security.
The following is a list of official PCI SPoC resources:
Related articles
This is a list of key events in the development of SPoC:
Standards documentation https://www.pcisecuritystandards.org/document_library
First labs approved

To accept credit cards in Canada, businesses need to be PCI compliant. Becoming PCI compliant can be difficult in the first place and keeping up...
![This Week’s [in]Security – Issue 80](https://www.controlgap.com/hubfs/Imported_Blog_Media/servers-security-news-700x525-2.jpg)
Welcome to This Week’s [in]Security - Facebook breach fallout and other troubles, rethinking privacy, PIN on COTS (SPoC) gets closer as SCRP devices...

Cardholder data, aka CHD, comes from credit, debit, and prepaid cards bearing the logo of one of the PCI founding card brands. CHD includes the...